Making the Website Public
09/06/25
Cloudflare Tunnel
After sorting out the previous issues with ufw I can now get back on track to one of the original goals which was making this website public. I looked into the options for this, VPN, port forwarding, etc, and I decided on using Cloudflare tunnel. For my needs, this was the easiest solution where I just need to expose my service securely.
This required me to install the Cloudflare daemon on my server and then create a tunnel in the Cloudflare web interface. I installed the Cloudflare daemon with their official Docker image and then set up a Cloudflare account and a subdomain to utilise a new tunnel (given that I changed to Cloudflare nameservers on my registrar). This required me to enter the local URL of the service that the tunnel would access which was http://website (the website's container). In order for the tunnel/daemon to access the service I created a new Docker network with docker network create "cloudflare-tunnel-net".
I ended up with a docker-compose.yml file along the lines of the following for the tunnel service:
services:
cloudflared:
image: cloudflare/cloudflared:latest
container_name: cloudflare_daemon
restart: always
command: tunnel run --token ${TUNNEL_TOKEN}
networks:
- cloudflare-tunnel-net
networks:
cloudflare-tunnel-net:
external: true
I also added the Docker network to my website's Docker Compose and then restarted the container as well as starting the tunnel container. I tried navigating to homelab.nicolldouglas.dev and surprisingly the site showed up without issue—mission accomplished at the behest of Cloudflare convenience.
About Tunnels
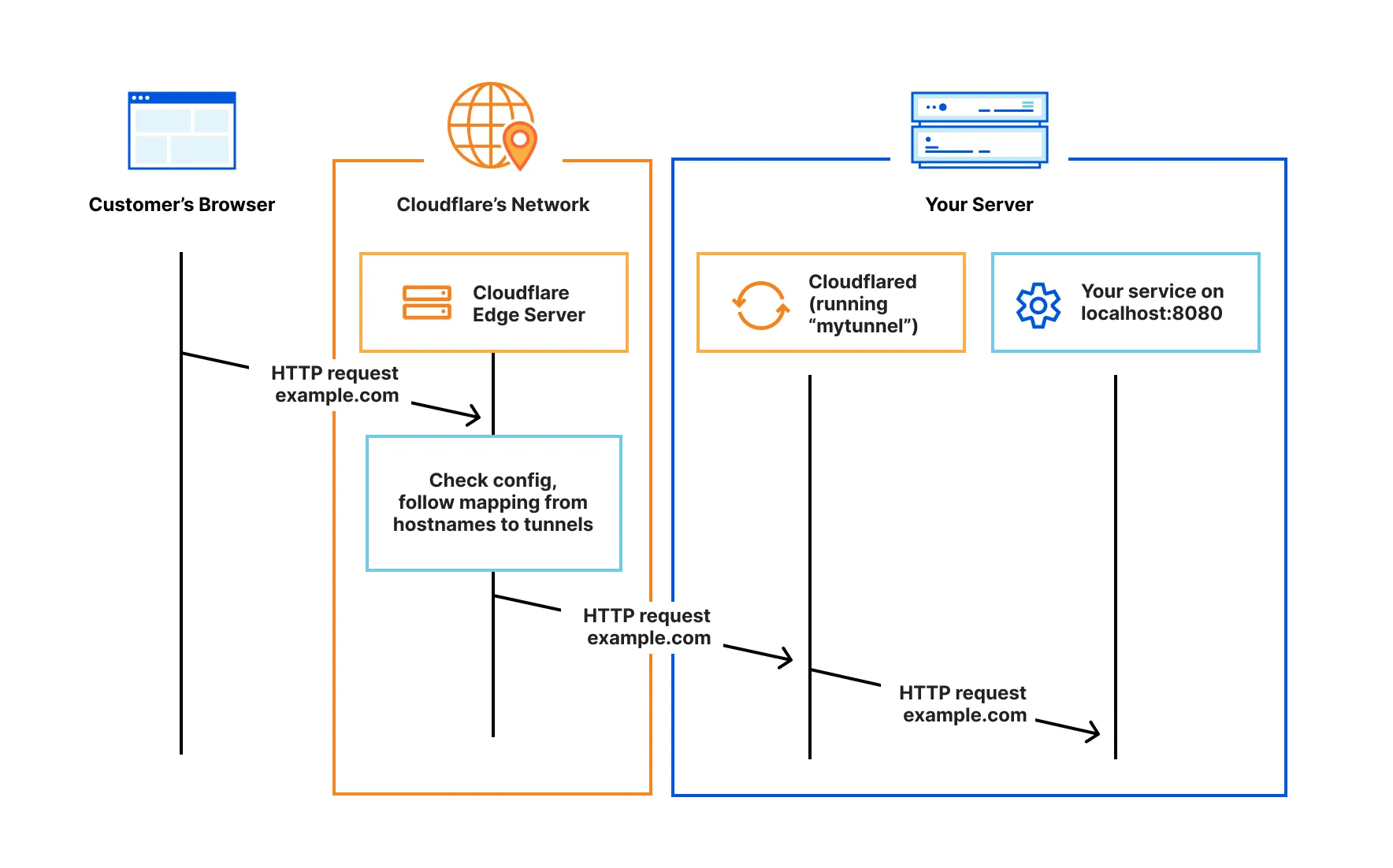
I found it interesting how tunnels actually work when reading the docs so I've decided to make some notes below on it:
- A tunnel to a machine is created by initiating an outbound connection from the machine to elsewhere.
- The connection is kept open in order to feed back other connections through it.
- The machine or network on the other end pipes through these connections as if they were responses to the original connection.
- No new inbound connections are ever made to your machine so there is no need for port forwarding or any other form of network exposure.
When it comes to Cloudflare tunnels, the image below from their docs sums it up pretty well:
But now this website has been successfully made public which is huge. The next goal is for me to set up some CI/CD with Gitea to automatically redeploy the site's Docker container when I push to main.